
The desire to manage, monitor and collect historical data for better and more reliable solutions has led companies to connect their devices and systems. You can now communicate with devices installed elsewhere in the country/world and data can be automatically downloaded to the control center for further analysis. This brings a lot of benefits, but it connects decentralized installations that were previously completely isolated from the outside world and didn't need much attention in terms of security.
But cyber security is now a threat and the number of cyber attacks is increasing every year as there is big money to be made for hackers. It is therefore important to focus on the security of your installation to avoid such fatal and costly attacks. But how can you do this?
While there are many standards and guidelines for cybersecurity, in this article we will focus on what many consider the three most important points: visualizing your network and security status, dividing the network into segments and securing the most critical devices.
We'll start by looking at how you can improve network visibility when performing configurations and operations, as well as how to respond to incidents and maintain the security of your network.
▎Configuration ▎
Follow security settings guidelines and visualize the status of your network
In our daily lives, we often see how surprisingly easy it is to hack an IP camera, for example, if the default password has not been changed. Therefore, we are encouraged to regularly update our passwords and implement other security features, such as two-factor authentication. The same logic applies to industrial applications. A breach occurs when the default password for industrial devices is not changed or the devices are used without adequate protection. As more devices become interconnected, the risk of one device being attacked and infected increases, giving hackers access to the entire network.
For a better understanding of how to secure your industrial devices, read our guide on Security optimization based on an NPort 5000.
Ensuring that industrial installations have adequate protection against cyberattacks often requires many hours spent reviewing the configurations of individual devices. One of the most effective ways to simplify this task is to use a network management program that allows you to quickly and visually see the status of your network security. Felipe Sabino Costa, ISA Cybersecurity Instructor and Moxa LATAM Industrial Cybersecurity Expert, explained in the white paper, A Systematic Approach to Checking Cybersecurity, that a systematic and automated approach to security configurations with a focus on vulnerable devices significantly reduces the likelihood of overlooking incorrect or incomplete configurations, which can happen when configurations are entered manually.

Visualize the security status of network devices by using different colors.
Once the software is installed, network administrators get a quick visual overview that shows if anything needs updating to ensure operations remain smooth and secure.
▎Operation ▎
Get a better overview of your industrial network
While digitalization has made it possible for people, machines and systems to be connected, it has unfortunately increased the possibility of introducing cybersecurity threats into the network. That's why it's important to know the real-time status of each device - and that goes for all activity on your network.
There are several ways to achieve this goal. First, dashboards that visually display real-time network and security activities are very useful for network administrators and security professionals. They need to gather the latest information and see it quickly. Secondly, it's important to save logs so you can later determine where and when an incident occurred. Thirdly, a regular backup mechanism is necessary so that after an attack, the installation can be restored as it was before the attack.
Visualizing your network allows you to get a better understanding of how your network is currently divided. Typically, in an installation there will be many devices, so having an overview allows you to design the network and improve your cybersecurity. One of Moxa's customers wanted to divide their network into smaller groups to achieve better cybersecurity. As they already had a visual overview of their network topology, this task was easy for them. To learn more, read more examples about safety here.
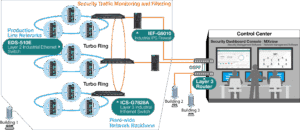
A real-world example of network segmentation that helped customers implement cybersecurity.
▎Response and maintenance ▎
Centralized security management increases response time
With the ways hackers attack becoming increasingly complex, it's worth remembering that cybersecurity is a never-ending task. Industrial networks need to be constantly monitored, maintained and updated to ensure that systems and devices have adequate protection. Once technicians have finished configuring the network, they should collect data and describe what is considered normal activity on the network. Using this information as baseline knowledge, administrators can observe if there is sudden activity on the network that is out of the ordinary.
In the industry, it is common to visually display pie or bar charts with different colors, commonly referred to as dashboards, that make it easy and clear for the operator to see if something is wrong, if there is a potentially dangerous activity on the network. The sooner such a threat is detected, the sooner you can start investigating what's wrong and hopefully fix it before fatal damage occurs.
As we mentioned earlier, the more devices installed on a network, the harder it becomes to ensure that all devices have the most up-to-date security policies. An effective method that also reduces the likelihood of errors occurring is to manage the different cybersecurity policies and updates in groups.

Updating patterns and enabling cybersecurity policies for a group of devices.
Securing industrial networks against cyberattacks is a complex task. As there is no crystal ball, we strongly recommend that companies and network administrators start from the three basic aspects mentioned above to strengthen their cyber security. Throughout this process, it's important to choose a secure network infrastructure that, on the one hand, allows your devices to connect and get the job done, but on the other hand, also protects the installation from cyberattacks.
Start by visualizing your industrial network and you're good to go. Moxa has a specific page on cybersecurity, here you can find more information.
Also visit the product pages for more information about MXview network management software and Security Dashboard Console security management software.
Freely translated into Danish from Moxa's article.